Dive into the world of Kubernetes and explore why Kubernetes is popular, who uses it, the best Kubernetes security tools, and why there is a skill shortage in Kubernetes security space. With businesses today focusing more on cloud environments, it is clear that those who can master diverse and distributed container-driven cloud architectures will drive digital enterprise in the future. This article will explore why Kubernetes security is essential, along with the skills gap and mushrooming job prospects in the Kubernetes security space.
With the emergence of Kubernetes, one of the most popular open-source container management platforms, the container market is taken by a storm. Without Kubernetes, organisations would find it challenging to deploy and manage containers manually using command-line tools on a large scale. In simple words, deploying a container or two might not be challenging, but a container orchestration tool becomes necessary when dealing with containers on a large scale. Kubernetes helps in planning, scaling, and managing large-scale operations.

(Image Source: Pixabay.com)
Kubernetes has widely enabled organisations to deploy containerised applications in a production environment. Moreover, it has made time-consuming tasks like deployment and management of containers more manageable. Indeed, the job board published new data on their website, which states that the employer demand for IT experts having Kubernetes experience is growing at a lightning pace, faster than the candidate interest.
Containers and Kubernetes are driving the job market demand for the past four years and are virtually synonymous with cloud-native development today. Between Oct 2015 and Oct 2019, Kubernetes job searches increased by 2,125%, while the job share per million grew by a whopping 2,141%.
Understanding Kubernetes
As defined by kubernetes.io, “Kubernetes is a portable, extensible, open-source platform for managing containerised workloads and services. It facilitates both declarative configuration and automation.” A container can be defined as a unit of software that can package the program code and dependencies so that the application can run reliably and quickly between various computing environments. It essentially means that Kubernetes, also known as K8s, is one of the most popular open-source platforms developers use for container management, orchestration, and automation.
Who Uses Kubernetes and Why
Kubernetes has slowly evolved as the default standard for container management and deployments. Since it offers various advantages, major cloud providers like Google Cloud, Amazon AWS, and Microsoft Azure offer support for Kubernetes.
Kubernetes is being used in different scenarios, including:
- In-house: Organisations are using Kubernetes to transform their in-house data centre into Kubernetes clusters.
- Cloud: Using Kubernetes, businesses can create and manage a network of VMs easily.
- Hybrid: Kubernetes can be used in organisations that aim to create a hybrid Kubernetes cluster environment where they can have both clusters in-house and on the cloud.
- Multi-Cloud: With Kubernetes, businesses can avoid vendor lock-in by using a multi-cloud environment and minimising risk.
- Automation: Kubernetes is used to automatically create new containers, remove existing ones during the deployment.
- Orchestration: With Kubernetes, you can use your local cloud, public cloud, or a multi-cloud environment for container management.
- Load Balancing: Kubernetes automates your load balancing on your servers to adjust the network traffic accordingly. No outside help or admin interference is needed.
- Secret Management: Store and manage sensitive data like passwords, OAuth tokens, and SSH keys securely using Kubernetes without exposing it to your stack configuration.
- Self-healing applications: Kubernetes monitors all the containers in the environment and replaces or kills the containers that don’t respond, making container management easy.
Kubernetes Security
While Kubernetes is well-established to handle container workloads effectively, security is not managed by Kubernetes. Hence, organisations need to invest in third-party tools to address security related to Kubernetes containers. When it comes to Kubernetes security, it is mainly based on these 4C’s, Cloud, Cluster, Container, and Code.
The code layer is the innermost layer of the Cloud native security model that gains from the strong defence provided by the other three layers (Cloud, Cluster, and Container). But unfortunately, if these three layers are not adequately secured, it’s impossible to provide adequate security to your codebase.
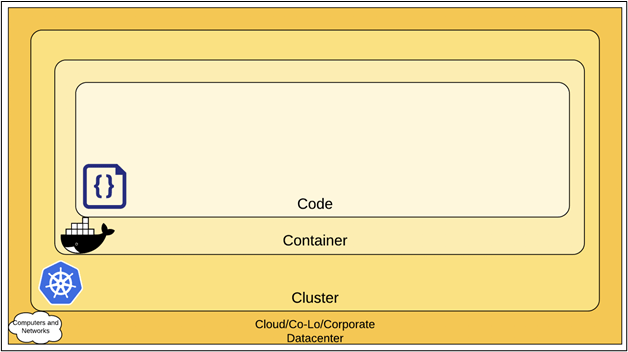
Image Source: (https://kubernetes.io)
What Is Driving the Emergence of Kubernetes Security?
In the State of Kubernetes Security report published by RedHat, 55% of respondents have reportedly said that they had to delay the rollout of the application due to security concerns. The report also states that 94% of respondents indicated that they faced at least one incident related to Kubernetes security. However, some factors make the adoption of Kubernetes security a must for enterprises. They are:
- Security – The top container strategy concern
Enterprises are eagerly adopting Kubernetes and containers because of the growing threat landscape. If they do not invest in security tooling and strategies simultaneously, there is a risk of security to their critical applications, which leads to a delay in application rollout.
- A robust community of contributors
According to the survey, there is 88% adoption of Kubernetes, with 74% in production environments. The robust community of contributors makes Kubernetes live up to the expectation of the de facto container orchestrator.
- Hybrid cloud deployments are more common
Over 47% of the respondents said they are running the containers in a hybrid environment v/s 28% said they run only in the public cloud. Since hybrid models are the dominant approach, they need security that works on the same line irrespective of the deployment of workloads.
- Misconfiguration – The leading cause of security incidents
Misconfiguration leads to the major cause of security incidents in most enterprises. Additionally, respondents cite human error as the leading cause of data hacks and breaches. While Kubernetes and containers may need significant configuration, they reduce this risk significantly.
While organisations are eager to implement Kubernetes, failure to invest in Kubernetes security will lead to vulnerability and security risks in their applications. Hence organisations are embracing DevSecOps and concentrating more on integrating security into their development life cycle. The report states 74% of organisations already have some DevSecOps initiatives.
Top Five Software Solutions Available in the Market for Kubernetes Security
While Kubernetes has made it simple to deploy and manage containers in large numbers, securing all your pods and containers is a risk one cannot take lightly. Many open-source software solutions are available in the market that will help you tackle container security issues effectively.
Given below is an overview of the six software solutions for Kubernetes security:
Prisma Cloud (formerly ‘Twistlock’) is an automated and scalable container security platform that includes a SaaS deployment option. It provides a full-lifecycle pipeline to perimeter security for your containerised environment. With Prisma Cloud compute, you can scale and deploy containers with ease without worrying about security. It offers vulnerability management, runtime protection and network security for containerized applications.
Aqua Security is another widely regarded Kubernetes container security platform that offers total visibility and control over your containerised environment. Aqua Security provides multi-tenancy management and advanced Kubernetes runtime protection, packed with intrusion detection and prevention capabilities.
Kube-bench is an open-source tool provided by the Center for Internet Security (CIS) for testing Kubernetes deployments to check whether they meet the CIS guidelines and benchmark tests. Besides testing, Kubernetes also provides concrete solutions to fix issues and vulnerabilities in the containerised environment.
Project Calico is an open-source container networking solution for Kubernetes that helps manage highly secure and scalable network policies. It helps in managing network connectivity and enforcing network security policies between workloads.
Kubeaudit is a command-line tool used for auditing Kubernetes clusters and ensures that you are deploying a secure cluster. The tool will check the cluster to find containers running as root, containers without a read-only file system, containers with sensitive host paths mounted, etc.
Kubesec.io is an open-source security scanning tool to scan Kubernetes resources like pods and clusters for vulnerabilities and risks. It helps in ensuring everything is correct with your Kubernetes deployment.
Skill Shortage in Kubernetes Security Space Leading to an Unprecedented Demand
The demand for qualified and experienced Kubernetes security professionals is rising as organisations continue to move towards cloud-native development. While the demand is increasing multi-fold, the supply is not equally good.
In a recent survey conducted by Canonical,
- The biggest challenge to Kubernetes adoption is the lack of in-house skills. Canonical summarises that it is a dominant factor that defines the mainstream adoption of the tech eventually. Despite the enormous skills gap, for an organisation, it becomes difficult to start with Kubernetes unless they:
• Hire an in-house expert (which is very rare to find)
• Invest money and time to train their operations staff with the new technology. Training is only one part of the job, and the difficult one is retaining these employees once they have mastered the latest technology because of their increased market value!
• Also, there is an inherent risk involved in adopting new technology if organisations don’t have the required expertise.
• Only 45% of people interviewed reportedly said to have used Kubernetes in production, and 15% stated to have used Kubernetes It means that around 85% are environments without Kubernetes. This percentage is significantly large and perhaps one of the reasons that it is slowly catching up with people leading to a shortage of skilled resources in Kubernetes Security.
Today, Containers and Kubernetes are virtually synonymous with cloud-native development. These technologies allow organisations to act fast, deploy software efficiently and carry out their operations unprecedentedly. From Youtube to Gmail to Search, practically everything at Google, for example, runs in containers.
But enterprises are finding it hard to fill these job positions. According to a StackRox survey, 540 security and IT professionals said that a steep learning curve and internal skills shortage is the most significant Kubernetes challenges that affect their enterprises.
Job Prospects
According to Kelsey Hightower, “Kubernetes is the sum of all the bash scripts and best practices that most system administrators would cobble together over time, presented as a single system behind a declarative set of APIs.” They include automation, centralised logging, monitoring, failover, etc. It builds on the inherent knowledge of the DevOps community, making it the default standard.
According to Indeed, technology giants like Microsoft, Verizon, Cisco, IBM, and VMware had the maximum Kubernetes job listings on their job board. It further adds that the following are the top tech roles related to Kubernetes jobs:
- DevOps engineers
- Software engineers/ senior software engineers
- Software architects
- Cloud engineers
- Full stack developers
Kubernetes is a relatively new technology; hence, before candidates apply for a Kubernetes-related job, they must have functional knowledge about the fundamentals. Kubernetes operates on entirely new technologies and environments. Therefore, a job seeker must know how to use it!
The employer will expect at least a year of experience and programming knowledge in specific languages for candidates aiming for engineering positions. The requirements are entirely different for those applying for non-engineering roles. Additionally, those seeking jobs in the customer success department must understand the needs of Kubernetes end-users and know specific use cases that can be helpful.
Many resources help candidates get started with containers and Kubernetes concepts and basics, which is a good starting point. But for the reasonably advanced skill set that Kubernetes requires, it’s helpful to be familiar with Linux, DevOps, and cloud tooling/methodologies before starting with Kubernetes.
Final Words
The adoption of Kubernetes is progressively increasing in the UK and Europe. Earlier, only the tech start-ups adopted Kubernetes, but now one can see an increasing trend in the broader market. While its use-cases make it flexible and adaptable in different environments, Kubernetes can be challenging to adopt initially due to the lack of skilled Kubernetes professionals. However, the growing job prospects and the rapid adoption of the technology certainly make it a lucrative career option for those seeking to apply their skills in maintaining enterprises’ information security.
References
- (2021, July 23). What is Kubernetes?
https://kubernetes.io/docs/concepts/overview/what-is-kubernetes/
- Casey, K. (2020). How to explain Kubernetes in plain English. The Enterprisers Project.
https://enterprisersproject.com/article/2017/10/how-explain-kubernetes-plain-english
- (2021, July 14). Kubernetes adoption, security, and market trends report 2021.
https://www.redhat.com/en/resources/kubernetes-adoption-security-market-trends-2021-overview
- The team, P. (2021). Canonical Survey highlights skills shortage in Kubernetes. Portainer.Io.
https://www.portainer.io/blog/canonical-survey-highlights-skills-shortage-in-kubernetes
- Chickowski, E. (2020). The Year Ahead for Kubernetes and Container Security. Business Insights.
https://businessinsights.bitdefender.com/the-year-ahead-for-kubernetes-and-container-security
- (2020). What is Kubernetes Container Security?
https://www.trendmicro.com/en_in/what-is/container-security/kubernetes.html
- Doerrfeld, B. (2021, June 19). 8+ open-source Kubernetes vulnerability scanners to consider. TechBeacon.
https://techbeacon.com/security/8-open-source-kubernetes-vulnerability-scanners-consider
- (2021, February 9). Top 10 Kubernetes Security Tools. Cloudplex.
https://cloudplex.io/blog/top-10-kubernetes-tools/
- Jonathan Greig. (2020, November 15). Experts share tips- how to get prepared for Kubernetes jobs.
https://www.techrepublic.com/article/experts-share-tips-on-how-to-get-prepared-for-kubernetes-jobs/
- (2020, February 19). StackRox Report Reveals that Container and Kubernetes Security Concerns are Inhibiting Business Innovation.
- Andrew Flowers. (2019, December 12). Indeed Tech Skills Explorer: Big Picture Tech Skill Trends. Hiring Lab.